How does a DDoS attack work?
I'm curious trying to understand how a DDoS attack works, for this I gave an online read and then wrote this snippet of code to attack my own router to see what happens:
import socket, threading
n = 0
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
def ataque():
global n, s
while True:
s.sendto(bytes(str(n),'utf-8'),('meu_ip',80))
n+=1
threading.Thread(target=ataque, args=()).start()
With threading I can check the value of n periodically being able to know how many packets have already been sent, but after a minute my computer crashes, there are several questions:
- How do I know the minimum time interval I have to include inside the
whileso that my pc does not crash during the attack? - which port is best for attack? I've tried using port 80, 21, 22, which I've seen others attacking but I don't know if there's a rule they use to determine it or if they're just popular.
- How do I know the attack is working?
- How do I know for another computer to recognize the attack? And how could I prevent it from another computer?
1 answers
DDOS the name already says it all (Distributed Denial of Service), it is a distributed attack coming from several IP'S(local), this type of attack simply clogs a service making the attacked server unable to respond requests, this will only happen if the power of sending requests of your robots exceed the processing limits of the attacked server.
So your test script cannot be considered a DDOS, Your Attack is not distributed, it is only coming from a single location...
How do I know the minimum time interval I have to include inside while so that my pc does not crash during the attack?
We have no way to answer, it will depend on the processing power of your PC, a distributed attack is infinitely more efficient, because you can for example "talk" to 1000 zombie robots (infected PCs in different places on the planet) send packets every 30 milliseconds, that is, a while with a time larger than not crashing your PC would be compensated for by the amount of zombies you have control of!
Which port is best for attack? I tried using port 80, 21, 22, I've seen others attacking but I don't know right if there's a rule that use to determine it or if they are only popular.
In theory any port that your Target Target has opened, each port in your example determines an open service, port (80) is attacked when you want to take a site from the ar, port 21 is attacked when you want to stop an FTP service, port (22) when you want to take down the SSH service...
How do I know the attack is working?
Vc will know when the port that is Attacking stops responding, if it is attacking port 80 and manages to undermine the entire processing power of the attacked server, no one will be able to access the site, simm vc caused a denial of service if this happens ...
As I know by another computer recognize the attack? And like me could you stop it from another computer?
First of all only the "owner" of the attacked network/server is able to prevent and identify something, if the attack is only a DOS, some PC alone sending requests within a while, it is relatively simple to contain the attack of a lobo solitário, a good firewall denying all packets from the attacker'S IP will contain the attack...But if the attack is distributed the request will come from many Different IP'S, sniffing the network and trying to find which IP's are sending requests as if there were no tomorrow is the output, with the IP's in hand you will have Q go blocking one by one in your Firewall, this type of action is time consuming, finding all the attackers in a distributed attack can take hours, this type of attack is really complicated to contain completely...
Follows a real example of attack happening on my server, it was a SYN-Flood on my port 80, I identified the attack practically at the same time as it began, I have connection control mechanisms by socket, I have automatic alerts that trigger emails, call, send SMS, etc., if a certain port has more connection than expected (my algorithm makes decisions based on the average of accesses that each port has, if this value extrapolates the alerts begin to be sent), this same algorithm adds the IP of the attacker in the firewall to be blocked, this type of attack in the Web server logs (apache, nginx, etc.), when such an attack happens (SYN flood-flood the port with SYN packets in an attempt to deny service), those who have access to the attacked server will be able to see several open SYN_RCVD connections, either using sniffers or looking at the access statistics on your server interface, a real example executed on my server at the time of]}
netstat -na | grep SYN_RCVD | awk '{print $5}' | cut -d. -f -4 | sort | uniq -c
232 222.93.XXX.XX
The Return told me I had 232 SYN_RCVD connections coming from the IP 222.93.XXX.XX
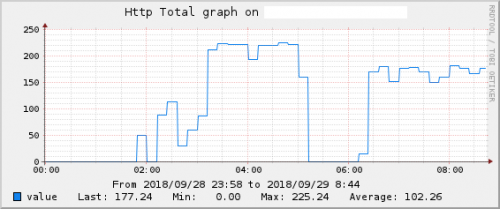
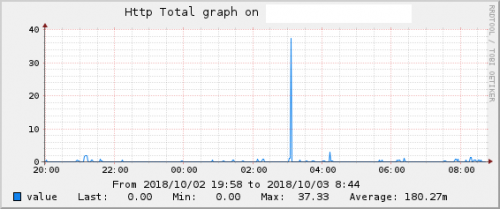
Follows a graph of monitoring the port 80 of my server, it is clear the discrepancy of accesses for when the attack began:
The first graph shows an attack happening, without connection control script, notice that for a long time had around 230 connections coming from the same IP, the second graph shows an attack attempt, had a connection peak of approximately 38 connections from the same IP, but the attack was contained after this peak by my algorithm!
This is a practical example of how I monitor and take action for attacks of this nature.
Usually DDOS or DOS send a flood of packets SYN-ACK, these packets consume resources of the attacked server, the packet is open waiting for a response until it reaches a time-out, that is, the packet is there occupying resource without ever being a response...